How to Build Professional Connections and Grow Your Career
How to build a strong professional network and grow your career with practical techniques and examples for career advancement and professional skills.

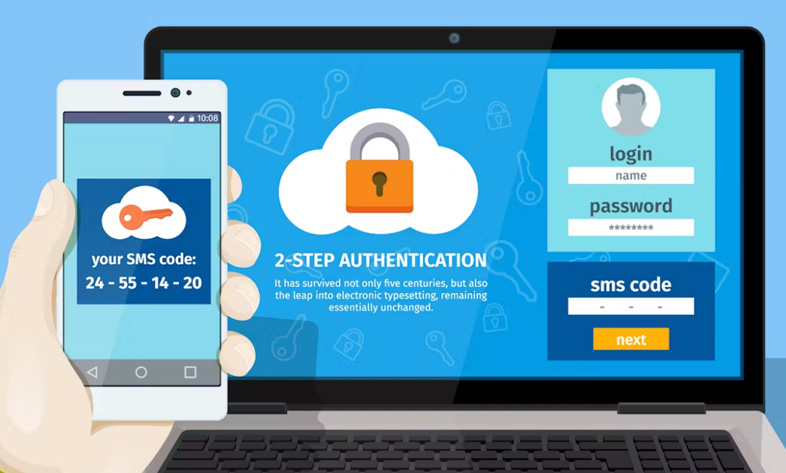
SMS-based two-step authentication can also be hacked. Big risk for bank accounts, social networks and all accounts that use it
Can two-factor authentication be hacked? Many people consider two-factor authentication to be a high level of information security.
But it's good to know that SMS-based two-step authentication can also be hacked.
Two-factor authentication is a security method used to protect personal and sensitive information.
This method allows users to verify their identity by entering their username and password, and then re-verify their identity by entering an additional code or other information.
Given the increase in cybercrime and hackers' infiltration of information systems, two-factor authentication allows users to ensure the security of their information.
This method is especially important for sensitive information such as banking information, emails, and other personal information.
With two-factor authentication, even if someone can get your username and password, they'll need access to a device or other information that only you have to log into your account.
This greatly reduces the possibility of hackers infiltrating personal accounts and ensures that your personal information is safe.
Overall, two-factor authentication is an effective way to increase online security.
With this method, users can ensure the safety of their personal information and enjoy the protection of their accounts from unauthorized access.
As a method of preventing cybercrime, two-factor authentication should be considered an essential tool in the security toolbox of every individual and organization.
One of the different methods of two-step authentication is using text message or phone call.
In this method, after entering a username and password, a text message containing a code or a phone call with a code is sent, which the person must enter in order to log in to their account.
This method of two-factor authentication is very effective because attacks that are carried out with only a username and password will not be able to penetrate a person's account.
Another method used for two-step authentication is to use special authentication software such as Google Authenticator or Authy.
These software generate a dynamic code that a person must enter to log in to their account.
This method is also very secure because the code generated by the software is only accessible on the individual's device, preventing unauthorized persons from accessing it.
One of the benefits of using two-factor authentication is increased account security.
This method reduces hacker attacks on a user account because even if the username and password are stolen, an authentication code is still required to log in to the account.
This greatly reduces the chance of unauthorized access to the user account.
Also, two-factor authentication reassures users that their account is more secure and their sensitive information is protected.
This increases users' trust in the service provider and creates positive marketing for companies.
However, using two-factor authentication also has its drawbacks.
One of its disadvantages is the increased time it takes to log in to your account.
Because to log in to your account, in addition to entering your username and password, you must also enter an authentication code, which may take time.
Also, some users may complain about the added complexity of two-factor authentication and prefer to use simpler methods of logging into their accounts.
Be aware that two-factor authentication is a big risk for bank accounts, social networks, and all accounts that use it. To learn how to prevent it and for more information on how to hack two-factor authentication, join itroz Academy.
Today, two-step authentication is used in many systems, for example, in social networks such as the most widely used ones, Instagram, Facebook, Twitter, Telegram, WhatsApp, as well as banking systems.
Many people believe that using two-factor authentication makes their account very secure and cannot be hacked. However, this is a very wrong idea and two-factor authentication is more vulnerable than any other method.
Two-factor authentication is a response to improving password security, which is commonly used on social networks.
But other services also use this mechanism, such as the Iranian banking system, which encourages users to use it to enhance the security of their accounts through a one-time OPT SMS system that expires after a short period of time.
Some people believe that this system cannot be penetrated, but we must warn that this system can be hacked and penetrated and can cause irreparable damage.
We would like to explain about two-step authentication hacking and methods to prevent it.
Today, offline services are very common, and SIM card replacement is a common service offered by telephone operators.
Hackers most often target the victim's financial goals through SIM swapping attacks, which is not an easy process.
For example, Bitcoin investor Michael Turpin lost 1,500 Bitcoins from his account after a SIM card swapping attack, and in another attack, journalist Matthew Miller was able to stop hackers before they could convert $25,000 from his account into Bitcoin.
If you are a victim of SIM card swapping attacks, immediately deactivate your SIM card through the operators' offline services.
To choose the appropriate two-step authentication method, you should consider the following points:
Considering these points, you can choose an appropriate two-step authentication method that provides both high security and ease of use for users.
Source » Itroz Academy

Follow the guide to set up your domain email on any device or OS, including both smartphones and computers, quickly and easily.

This guide is useful for automatically forwarding your website emails set up on your domain to other email accounts, such as Gmail and others.
Comments (0)